In the ever-evolving world of technology, Linux distributions have emerged as the backbone of countless systems and applications. However, recent developments in the form of immutable Linux distributions have gained significant attention within the tech community. Immutable Linux distributions offer a fresh approach to system management, emphasizing enhanced security, reliability, and scalability. In this article, we will explore why immutable Linux distributions are important and how they could shape the future of computing.
I strongly believe that this is also an integral part of flag theory (cf. Advocating for the decentralization of all systems and structures) to safeguard privacy and enhance personal security.
Introduction to Immutable concepts
- Understanding Immutable Linux Distributions: Immutable Linux distributions are built on the concept that once deployed, their core components remain unchanged throughout their lifespan. Unlike traditional Linux distributions where updates and modifications can be made at runtime, immutable distributions enforce immutability by design. This means that any changes or updates are only applied during initial deployment or through systematic upgrades.
- Enhanced Security: One of the primary reasons why immutable Linux distributions are gaining traction is their ability to enhance system security. By eliminating runtime modifications to critical components, these distributions minimize attack vectors for cybercriminals seeking to exploit vulnerabilities in live systems. With an immutable infrastructure in place, potential threats are significantly reduced as there is no possibility for unauthorized tampering with vital system files.
- Reliability and Stability: Immutable distributions provide unparalleled reliability and stability due to their inherent nature of preserving a consistent state throughout their lifecycle. The absence of runtime modifications ensures that software dependencies remain intact, reducing compatibility issues that may arise during updates or changes on traditional systems. As a result, users can experience more reliable performance with minimal downtime caused by unexpected errors or conflicts.
- Simplified Maintenance: Immutable Linux distributions simplify system maintenance by streamlining updates and patches through image-based deployments or rolling releases. Rather than manually applying individual patches across numerous running instances, administrators can deploy updated images across their infrastructure efficiently and consistently. This approach not only saves time but also reduces potential human errors that may occur during the update process.
- Scalability and Reproducibility: With the rise of cloud computing and containerization technologies, scalability has become a crucial factor in modern computing environments. Immutable Linux distributions embrace this paradigm by enabling seamless scaling through the deployment of consistent images across multiple instances. Moreover, the immutable nature ensures consistent results, making it easier to reproduce various environments, facilitating development, testing, and deployment processes.
- Future Potential: Given the increasing demand for enhanced security, reliable systems, and simplified maintenance, immutable Linux distributions are well-positioned to shape the future of computing. As technology advances and more organizations adopt cloud-native architectures and containerization, immutable distributions offer a logical step forward towards achieving improved security postures and operational efficiency.
A comparison of immutable vs. mutable concepts
When it comes to operating systems, there are two main categories: immutable and mutable. The comparison between these two types can shed light on their key differences and advantages.
In an immutable operating system, updates are applied at reboot. This means that any changes made to the system only take effect after a restart. Additionally, the root partition, which contains essential system files, is set as read-only, preventing any modifications to its contents. Immutable systems are considered extremely secure since they limit the potential for unauthorized changes or malware infections.
On the other hand, mutable operating systems offer more flexibility and allow updates to be applied in a live environment. This means that changes can take effect immediately without requiring a reboot. In mutable systems, the contents of the root partition can be modified as needed.
In terms of installing applications, immutable systems often rely on technologies like Flatpaks, Snaps, and AppImages.
Mutable systems primarily use package managers such as APT (Advanced Package Tool), DNF (Dandified Yum), Pacman, and Zypper to install applications. However, they also support alternative package formats like like Flatpaks, Snaps, and AppImages. These package formats provide a way to install software independently of the underlying system and ensure compatibility across different distributions.
In summary, while immutable operating systems prioritize security by applying updates at reboot and locking down the root partition, mutable systems offer more flexibility by allowing live updates and modifications to system files. The choice between these two types depends on specific needs and preferences in terms of security versus flexibility in an operating system.
Example: Vanilla OS
Vanilla OS is a unique operating system built upon the principles of immutability, offering a range of benefits and features. Developed by a team of skilled engineers and software architects like Mirko Brombin or Pietro Di Caprio, as Immutable Linux Distribution it of course has the same advantages as mentioned in the beginning of this article.
Nevertheless there are a couple additional things I would like to highlight.
- The OS is built on an open-source Linux distribution, taking advantage of community-driven development and collaboration. Vanilla OS Kinetic is based on Ubuntu, Vanilla OS Orchid is based on Debian Sid
- The open-source foundation provides the reliability and flexibility associated with Linux systems. The system also integrates with containerization technologies like Docker or Kubernetes due to its immutable nature. This compatibility allows for efficient deployment and scaling of applications in isolated environments without compromising system stability.
- The system offers the flexibility to use various package formats, including Flatpak, AppImage, and soon Snap. This allows users to easily install and manage applications using their preferred packaging system.
- In addition to supporting external package formats, Vanilla OS provides its own package manager called apx. This command-line tool allows users to install packages from Ubuntu, Fedora, or Arch Linux repositories within isolated containers, providing a secure and sandboxed environment for software installation.
- Furthermore, apx extends its support to internal packages based on Nix. By initializing Nix with
apx init --nix, users can take advantage of this functionality. For instance, runningapx install --nix htopwould enable the installation of htop using the Nix package manager. - Underlying apx is a subsystem called Distrobox which leverages either Podman or Docker container engines. This powerful combination enables the creation and management of containers used by apx for installing and running software packages.
- Furthermore, apx extends its support to internal packages based on Nix. By initializing Nix with
- ABRoot (documentation) is a utility offered by Vanilla OS, guarantees the integrity and stability of the Linux system through complete immutability and atomicity. It achieves this by managing two separate root filesystems and performing updates using OCI (Open Container Initiative) images. This ensures that the system remains in a consistent state even during updates.
- VSO is a powerful utility designed specifically for performing maintenance tasks on Vanilla OS installations. With VSO, users can easily manage and optimize their Vanilla OS setup.
- During the installation process, users have the option to include support for proprietary Nvidia graphics drivers in Vanilla OS. This feature comes with a dedicated official image that comes pre-installed and pre-configured for seamless integration with Nvidia hardware.
In addition to its focus on immutability and security, Vanilla OS prioritizes a user-friendly interface that is intuitive to navigate. It offers a familiar experience for both novice and experienced users alike.
Source: YouTube
VSO & APX in further detail
Updates in Vanilla OS are handled by VSO (Vanilla System Operator), which manages the operating system. VSO performs weekly or monthly updates in the background without any user intervention. Since Vanilla OS is a transactional system, the updates are applied only after a reboot.
- Check the current configuration:
sudo vso config show - Check a specific option:
sudo vso config get update.smart - Update a specific option:
sudo vso config set update.smart true - Check for an update:
sudo vso update-check - Force an update:
sudo vso trigger-upgrade —now
Install and manage applications
In the commands below, <package_manager> will be a placeholder. It can be replaced by the following options:
apt,dnf,aur,apk,zypper,xbps,nix
Furthermore examples
- Container creation: `apx init --<package_manager>‘
- Install apps:
apx install --<package_manager> <package> - Install DEB packages:
apx install --sideload <path/to/package.deb> - Install RPM packages:
apx install --dnf --sideload <path/to/package.rpm> - Add desktop entry:
apx export --<package_manager> <package> - Uninstall apps:
apx remove <packages> - Detect and remove the desktop file entry:
apx unexport --<package_manager> <package>
Changes with APX v2
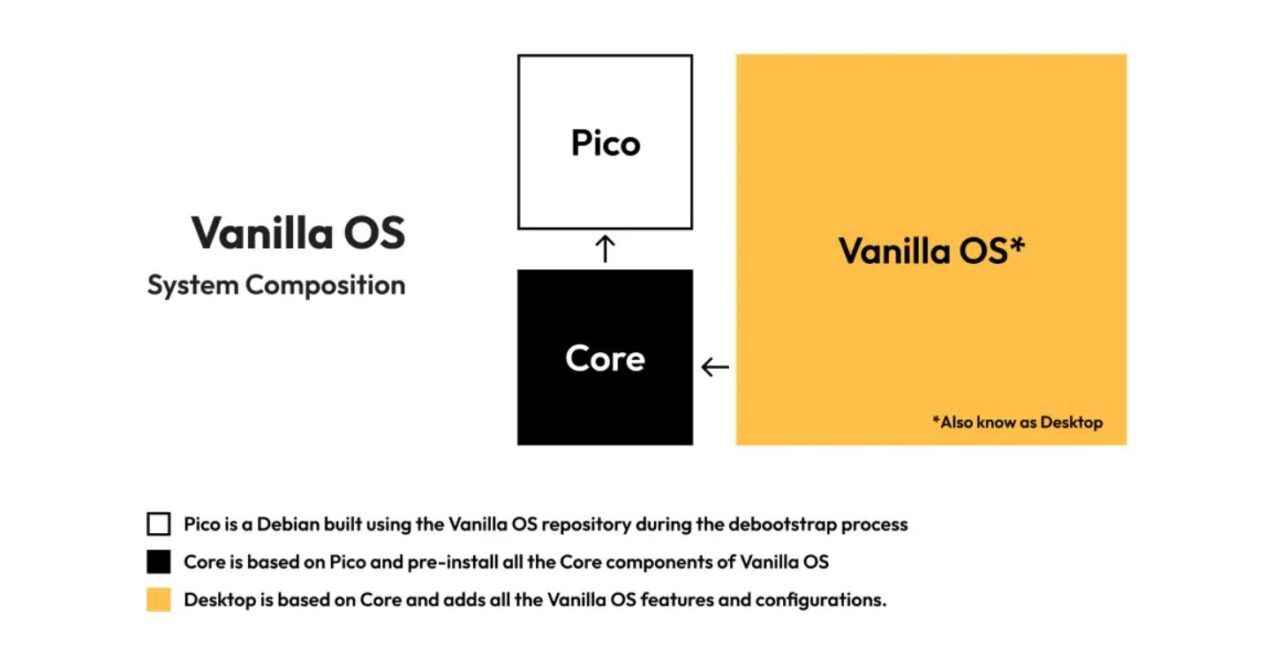
APX v1 was able to install packages from different distributions using flags such as --dnf for Fedora or --zypper for openSUSE. APX v2 still offers this capability, but in the form of stacks that can be configured based on the user's needs.
A stack is a set of instructions that can configure an environment based on any Linux distribution by adding packages and settings at the user's discretion. The user can create a new stack at any time by specifying a base Linux distribution, such as Arch Linux, and an optional list of packages. With this stack, the user can start one or more new subsystems based on this stack.
After creating a subsystem, the user can utilize package manager commands (such as install, remove, update) or access the subsystem similar to APX v1. The collaborative use of stacks is also possible. APX v2 offers a collection of pre-configured stacks for easy access to major Linux distributions.
This new structure allows users to create stacks tailored for specific purposes. For instance, a stack can be created with all the necessary tools and libraries needed for development in various fields like 3D applications, music production, programming, and more. In case of any issues, the subsystem can be restored by reinitializing it and returning it to its original state defined by the stack.
Stacks serve as templates for generating a subsystem. Those define the following fields:
- Name
- Base: This refers to the original distribution to use for the subsystem.
- Package manager: It is the package manager to be used within the subsystem to expose commands such as install, remove, etc.
- Packages: An optional list of packages to be pre-installed when creating the subsystem.
Package managers are not just names in Apx v2; they are actual entities. Each package manager exposes the relationships between the standard Apx commands (install, remove, update, etc.) and the original command of the package manager itself.
Both entities are stored as Yaml files and stacks can be imported/exported using the commands:
apx stacks import -n [name]
apx stacks export -n [name]
ABRoot v2
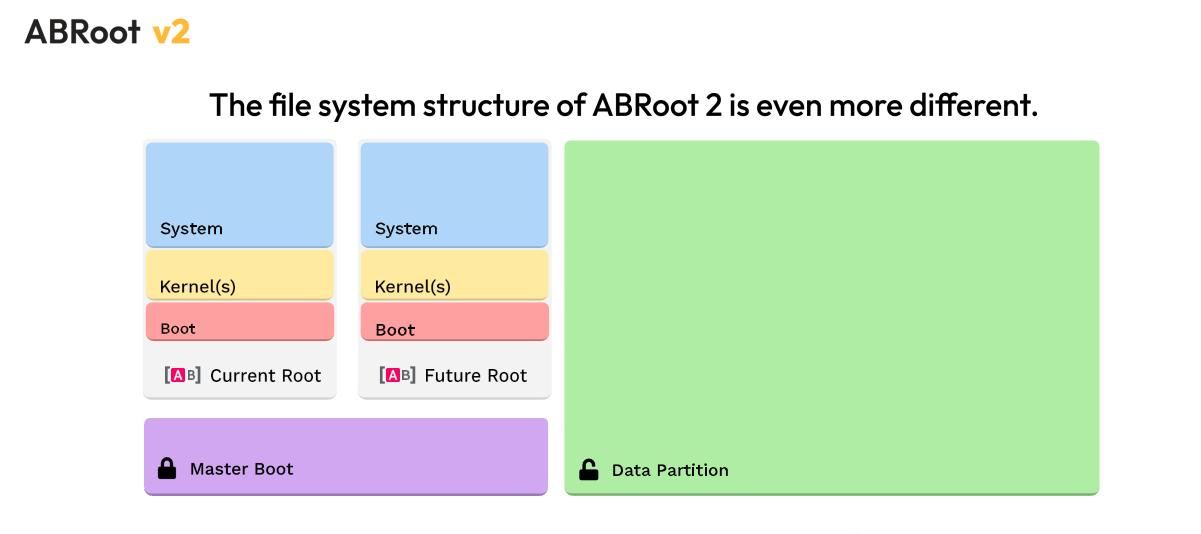
For "Orchid", ABRoot has been significantly enhanced to ABRoot v2. The new version is not just an update, but the entire underlying structure has been completely rethought and rewritten to provide the ideal solution for all use cases by using images in the OCI-Image-Format of the Open Container Initiative.
To install additional packages outside of the immutable base system, Version 1 introduced the package manager APX derived from APT and Distrobox, which could install additional software in its own containers. With Vanilla OS 2, this functionality is migrated to ABRoot v2 into a package manager that allows users to manage such packages using atomic transactions.
abroot pkg add <your-package>
abroot pkg remove <your-package>
abroot pkg apply
This creates a local image of the latest Vanilla OS version, with the desired packages added or removed. This new local image is automatically kept up-to-date with the latest versions of Vanilla OS, thereby reducing complexity.
Final thoughts
This is the first part of a series of Immutable OS that I am currently using. There will be further articles on NixOS and Talos OS. Additionally feel free to check out one of the following alternatives yourself: Fedora Silverblue, EndlessOS, openSUSE MicroOS.
Immutable Linux distributions offer a promising solution to address critical challenges faced by traditional Linux systems. By emphasizing security, reliability, simplified maintenance, scalability, and reproducibility, they provide a solid foundation for future-proofing our computing environments. As organizations strive for robust systems that can withstand evolving cyber threats while ensuring uninterrupted service delivery, embracing immutable Linux distributions appears to be an essential step towards building a secure and sustainable future in technology.
The website and the information contained therein are not intended to be a source of advice or credit analysis with respect to the material presented, and the information and/or documents contained on this website do not constitute investment advice.

